About Rocheston
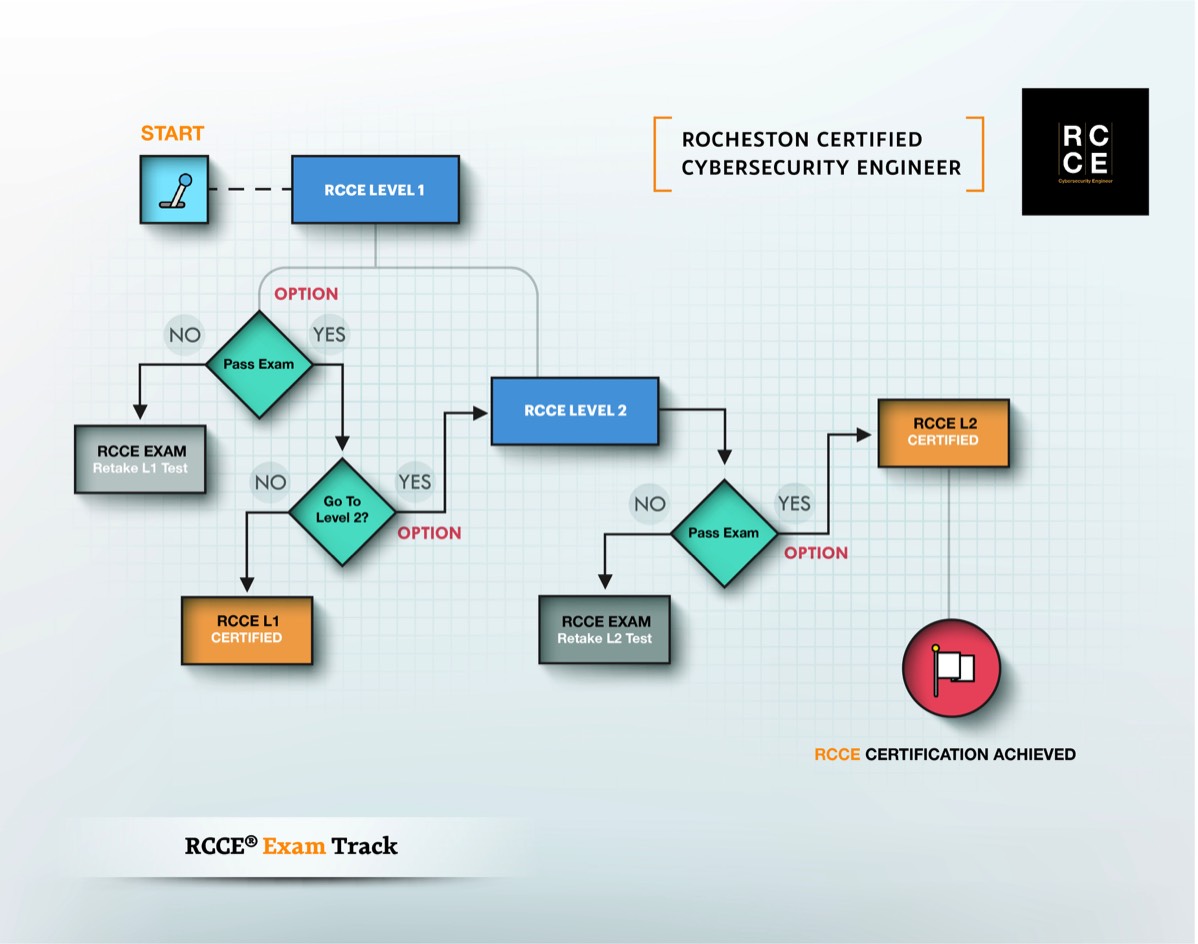
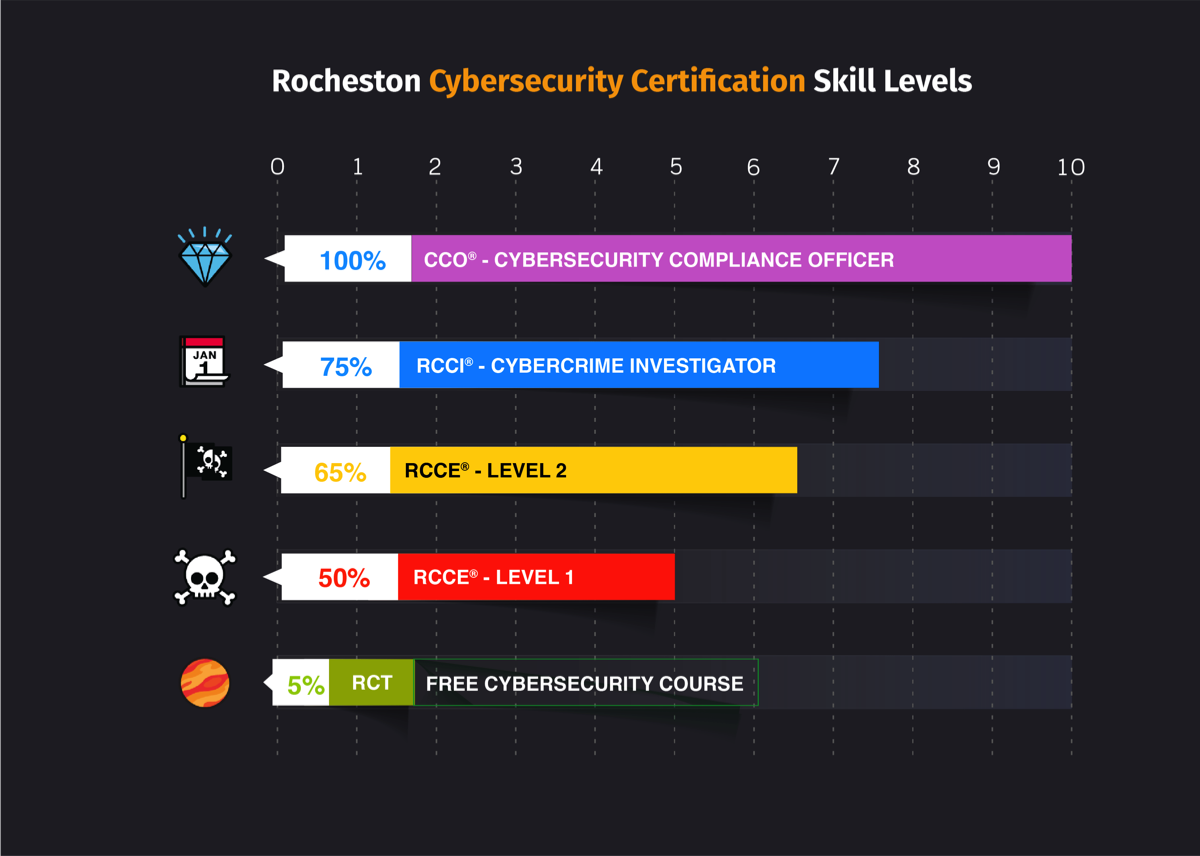
The Rocheston Department of Certification (RDoC), a division of Rocheston fulfills the mission of developing a certification examination for cybersecurity engineers. The Rocheston Certified Cyber Security Engineer (RCCE) examination being conducted since 2019 is one such step that provides its certification program for practitioners of cybersecurity engineer.
Over these years, multiple steps have been taken to develop, improve and streamline the resources required, the processes to be implemented and the values that needs to be strengthened. Support and assistance of cybersecurity engineer experts and psyshometricians have been a boon in shaping up a robust and competent structure.
The RCCE exam is provided multiple forms (separate question banks). Each form is psychometrically analyzed and has gone through rigorous beta testing with a sample target group, under the supervision of subject matter experts and psychometric analysts to ensure the RCCE exam is academically defensible and conforms to test development standards. The entire test development cycle was carried out to ensure candidates appearing for the certification program are tested on domains that are relevant in the real world.
Each form has been developed with an equal difficulty level to ensure equal assessment standards. The passing score is the same across the multiple forms.
The RCCE exam tests candidates on four domains- Domain 1: Cybersecurity Policies and Governance
- Domain 2: Risks/Threats/Vulnerability Assessment
- Domain 3: Risks/Threats/Vulnerability Management
- Domain 4: Security Incident Response and Recovery Plan
Technical areas covered under these domains
- 1. Cybersecurity Threats, Attacks and Defenses
- 2. Reconnaissance, ML and Artificial Intelligence
- 3. Cyber Vulnerabilities
- 4. Web Application Attacks
- 5. Webshells, Spywares and Trojans
- 6 Denial of Service Attacks
- 7. Log Management and Network Analyzers
- 8. Identity and Access Management
- 9. Wireless and 5G
- 10. Firewalls, Endpoint Detection and Response
- 11. Hacking Frameworks
- 12. Cryptography
- 13. Malware Analysis
- 14. IoT Security
- 15. Virtualization and Data Centers
- 16. Android hacking
- 17. Blockchain and Cryptocurrency
- 18. Quantum Computing
- 19: Cybersecurity Policies and Governance
- 20 Risk Assessment
- 21. Risk Management
- 22. Incident Response and Handling
- 23. DevSecOps
- 24. Patch Management
- 25. Cloud Security with AWS, Azure and GCloud
- 26. Rocheston Cybersecurity Framework
- 27. Zero Trust Architecture